Wazuh和n8n配合可以很方便的对安全事件进行编排处理。
n8n配置
选择webhook类型接收节点,post类型,Authentication可以先不配置,选择None。 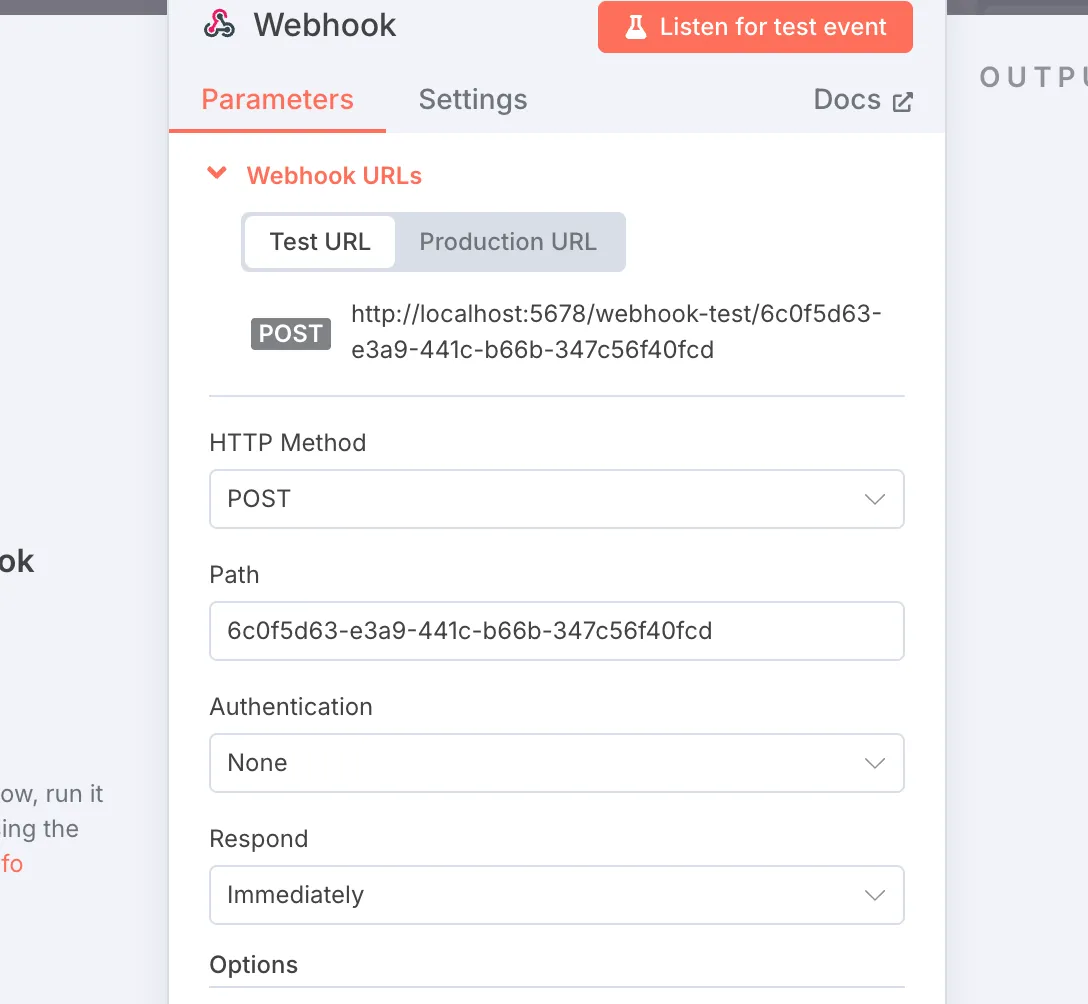
Wazuh发送到n8n的脚本
进行入wazuh的integrations目录
cd /var/ossec/integrations
wazuh自定义脚本必须以custom-打头。
编写n8n的shell脚本如下, custom-n8n的shell脚本是用来调用同级目录下的custom-n8n.py。
custom-n8n shell脚本
root@dev:/var/ossec/integrations# cat custom-n8n
#!/bin/sh
WPYTHON_BIN="framework/python/bin/python3"
SCRIPT_PATH_NAME="$0"
DIR_NAME="$(cd $(dirname ${SCRIPT_PATH_NAME}); pwd -P)"
SCRIPT_NAME="$(basename ${SCRIPT_PATH_NAME})"
case ${DIR_NAME} in
*/active-response/bin | */wodles*)
if [ -z "${WAZUH_PATH}" ]; then
WAZUH_PATH="$(cd ${DIR_NAME}/../..; pwd)"
fi
PYTHON_SCRIPT="${DIR_NAME}/${SCRIPT_NAME}.py"
;;
*/bin)
if [ -z "${WAZUH_PATH}" ]; then
WAZUH_PATH="$(cd ${DIR_NAME}/..; pwd)"
fi
PYTHON_SCRIPT="${WAZUH_PATH}/framework/scripts/$(echo ${SCRIPT_NAME} | sed 's/\-/_/g').py"
;;
*/integrations)
if [ -z "${WAZUH_PATH}" ]; then
WAZUH_PATH="$(cd ${DIR_NAME}/..; pwd)"
fi
PYTHON_SCRIPT="${DIR_NAME}/${SCRIPT_NAME}.py"
;;
esac
${WAZUH_PATH}/${WPYTHON_BIN} ${PYTHON_SCRIPT} "$@"
root@dev:/var/ossec/integrations# custom-n8n python脚本
再看看custom-n8n.py的内容。custom-n8n.py被custom-n8n的shell脚步调用
#/usr/bin/env python3
import sys
import requests
import json
from requests.auth import HTTPBasicAuth
# read configuration
alert_file = sys.argv[1]
user = sys.argv[2].split(":")[0]
hook_url = sys.argv[3]
# read alert file
with open(alert_file) as f:
alert_json = json.loads(f.read())
# extract alert fields
alert_level = alert_json["rule"]["level"]
# agent details
if "agentless" in alert_json:
agent_ = "agentless"
else:
agent_ = alert_json["agent"]["name"]
full_log = alert_json["full_log"]
# combine message details
payload = json.dumps({
"content": [
{
"title": f"Wazuh Alert - Rule {alert_json['rule']['id']}",
"description": alert_json["rule"]["description"],
"full_log": full_log,
"fields": [{
"name": "Agent",
"value": agent_,
"inline": True
}]
}
]
})
# send alert to n8n webhook
r = requests.post(hook_url, data=payload, headers={"content-type": "application/json"})
sys.exit(0)需要配置权限
chmod 750 /var/ossec/integrations/custom-n8n
chown root:wazuh /var/ossec/integrations/custom-n8nWazuh集成脚本配置
hook_url我们用上面n8n节点的url即可。
root@dev:~# cat /var/ossec/etc/ossec.conf
<ossec_config>
.......
<integration>
<name>custom-n8n</name>
<hook_url>http://localhost:5678/webhook/67f8sdfd34-8943-45fa-b5eb-10fc090e0</hook_url>
<alert_format>json</alert_format>
<level>10</level>
</integration>
......
</ossec_config>
